40 dmz network diagram example
Here are some examples. ... Visit blog post about UML diagrams; Network diagram. Illustrate the structure of your network. Click for live example; Venn diagram. Show the logical relationships between groups. Click for live example; Visit blog post about Venn diagrams; AWS diagram. Fully document your AWS network architecture. Figuring out how to diagram a network f o r the first time was a bit overwhelming, but what helped was to understand the borders and components of the external (public), demilitarized zone ...
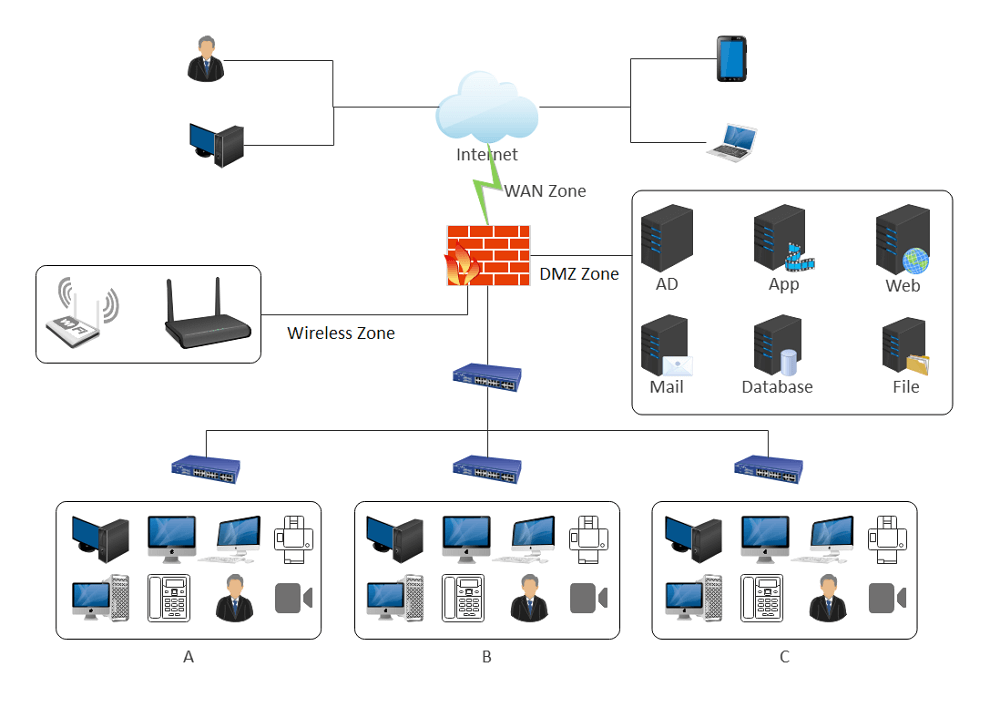
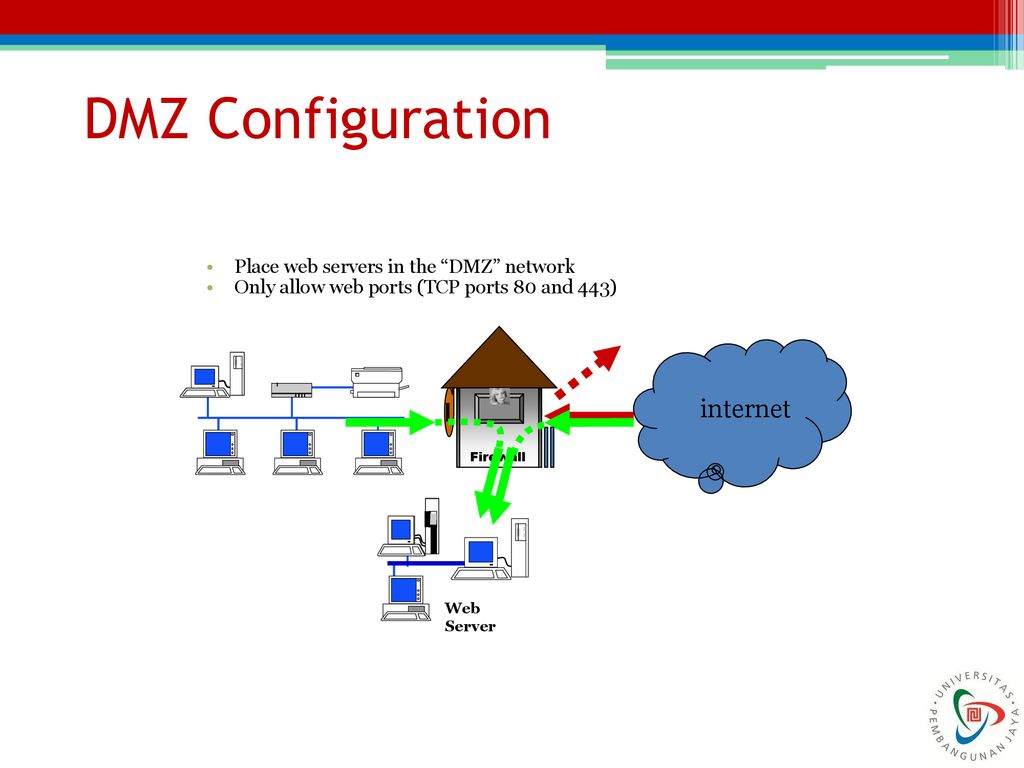
A DMZ network, in computing terms, is a subnetwork that shears public-facing services from private versions. When implemented correctly, a DMZ network should reduce the risk of a catastrophic data breach. Public-facing servers sit within the DMZ, but they communicate with databases protected by firewalls.

Dmz network diagram example
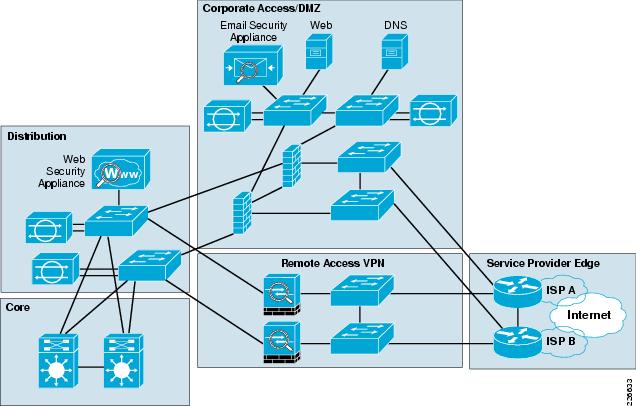
The diagram highlights the simple traffic paths: outside can access the DMZ server but not the internal hosts, and if hosts need to access the DMZ they can. Moreover, the default interface level policy will not allow the untrusted network to source traffic towards the trusted network. Download scientific diagram | A medium size network with a DMZ. from publication: Improving ... Table 1 An example of rules on the Listed-Rule firewall. You will need to have a 3rd Ethernet port available in order to create another physical network. This physical network example uses 3 ports: 1 for the WAN, 1 for the LAN, and 1 for the DMZ network. Assign DMZ Interface. To assign a new interface for the DMZ network, go to the "Interfaces > Assignments" page.
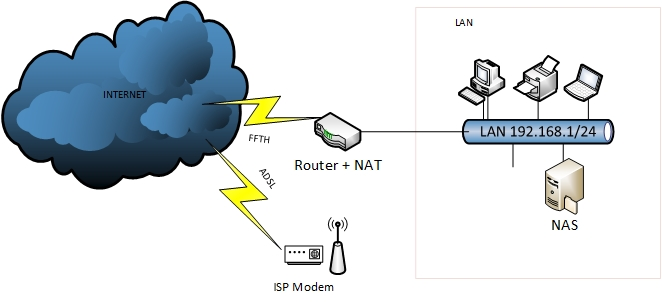
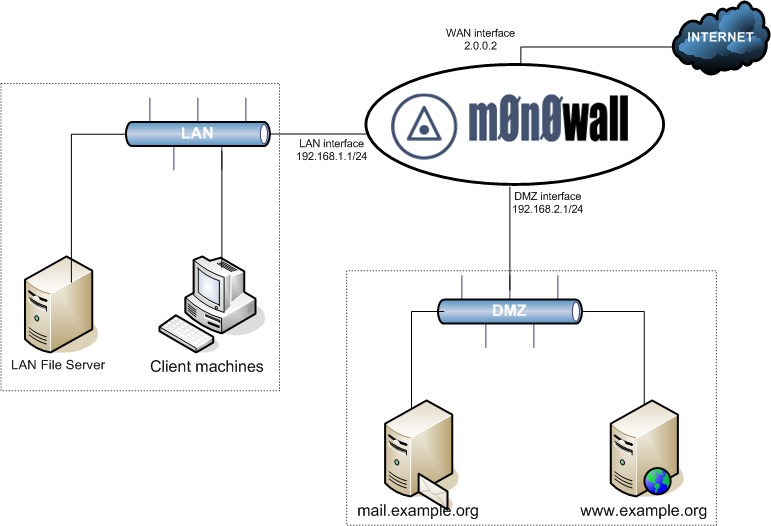
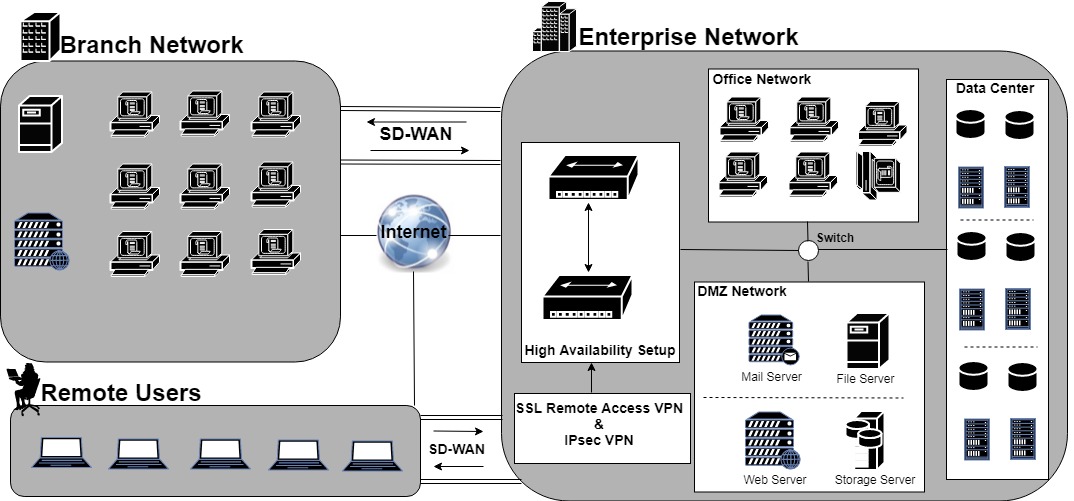
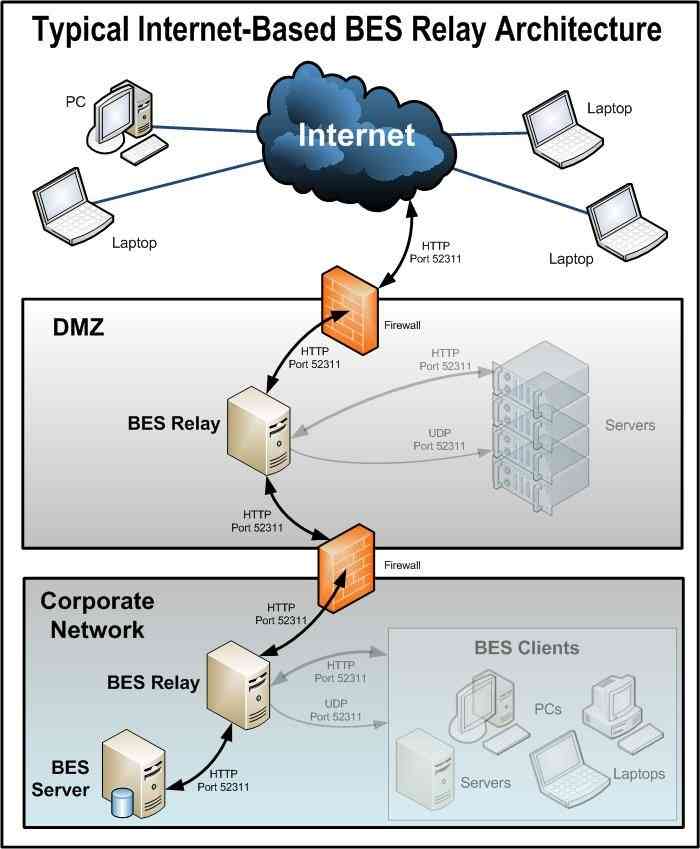
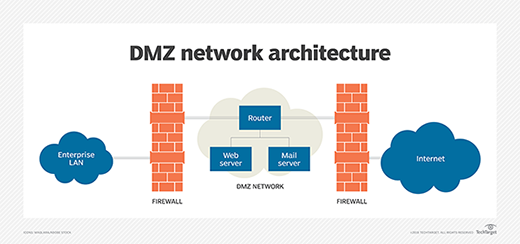
Dmz network diagram example. The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone ( DMZ ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network ). For example, you can allow HTTP to the Web-server on your DMZ, but not allow HTTP to your internal network. Systems in the DMZ should be as securely locked down as you can make them. Implement a secure hybrid network. This reference architecture shows a secure hybrid network that extends an on-premises network to Azure. The architecture implements a DMZ, also called a perimeter network, between the on-premises network and an Azure virtual network. All inbound and outbound traffic passes through Azure Firewall. A DMZ Network is a perimeter network that protects and adds an extra layer of security to an organization's internal local-area network from untrusted traffic. A common DMZ is a subnetwork that sits between the public internet and private networks. The end goal of a DMZ is to allow an organization to access untrusted networks, such as the internet, while ensuring its private network or LAN ...
Simple DMZ [classic] Use Creately's easy online diagram editor to edit this diagram, collaborate with others and export results to multiple image formats. You can edit this template and create your own diagram. Creately diagrams can be exported and added to Word, PPT (powerpoint), Excel, Visio or any other document. The example of the network diagram below shows network architecture with configuration called "two firewall demilitarized zone". Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network). It prevents outside users from gaining direct access to an ... h. Other services could be permitted into the DMZ network in the future. However, at this time, no other traffic is to be permitted into the DMZ network. Therefore enter the following: GAD(config)#access-list 112 deny ip any any i. Apply the outbound access-list to the DMZ network Fast Ethernet port. GAD(config)#interface fa 0 DMZ ( Network Diagram) Use Creately's easy online diagram editor to edit this diagram, collaborate with others and export results to multiple image formats. We were unable to load the diagram. You can edit this template on Creately's Visual Workspace to get started quickly. Adapt it to suit your needs by changing text and adding colors, icons ...
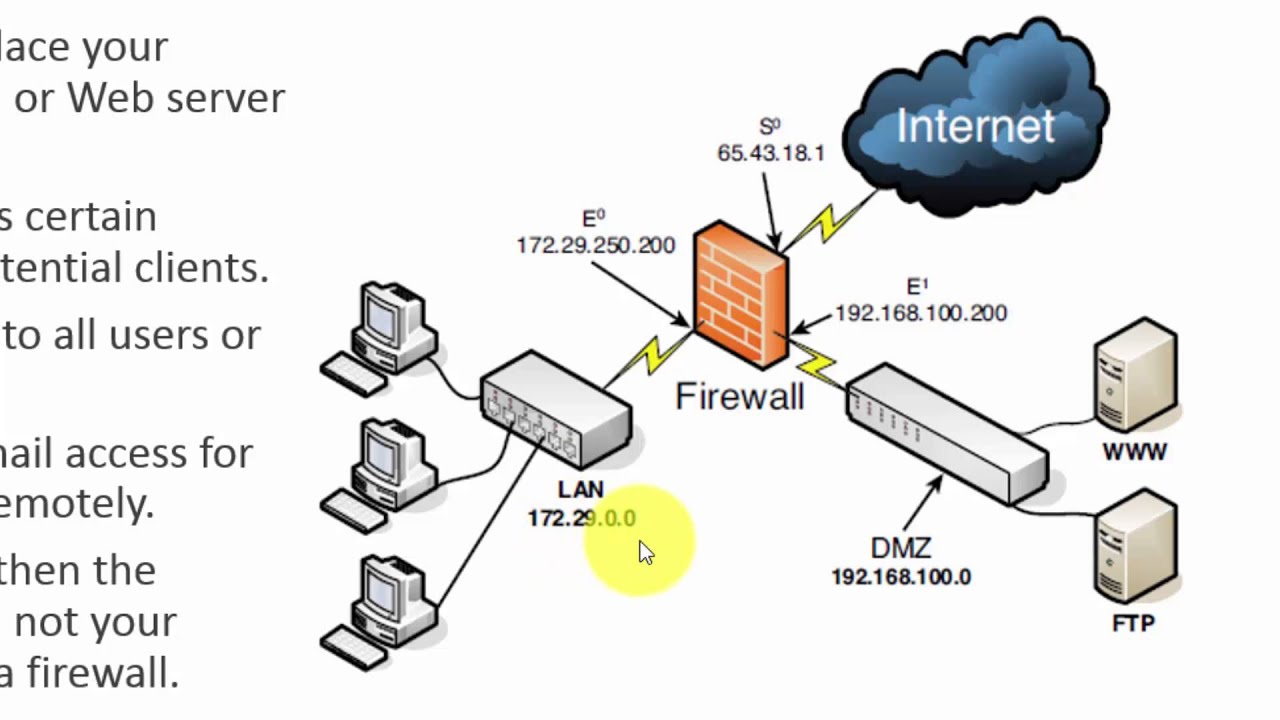
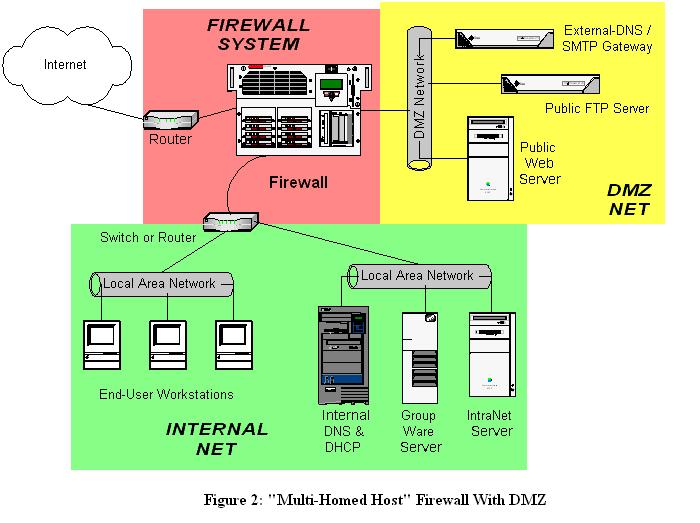
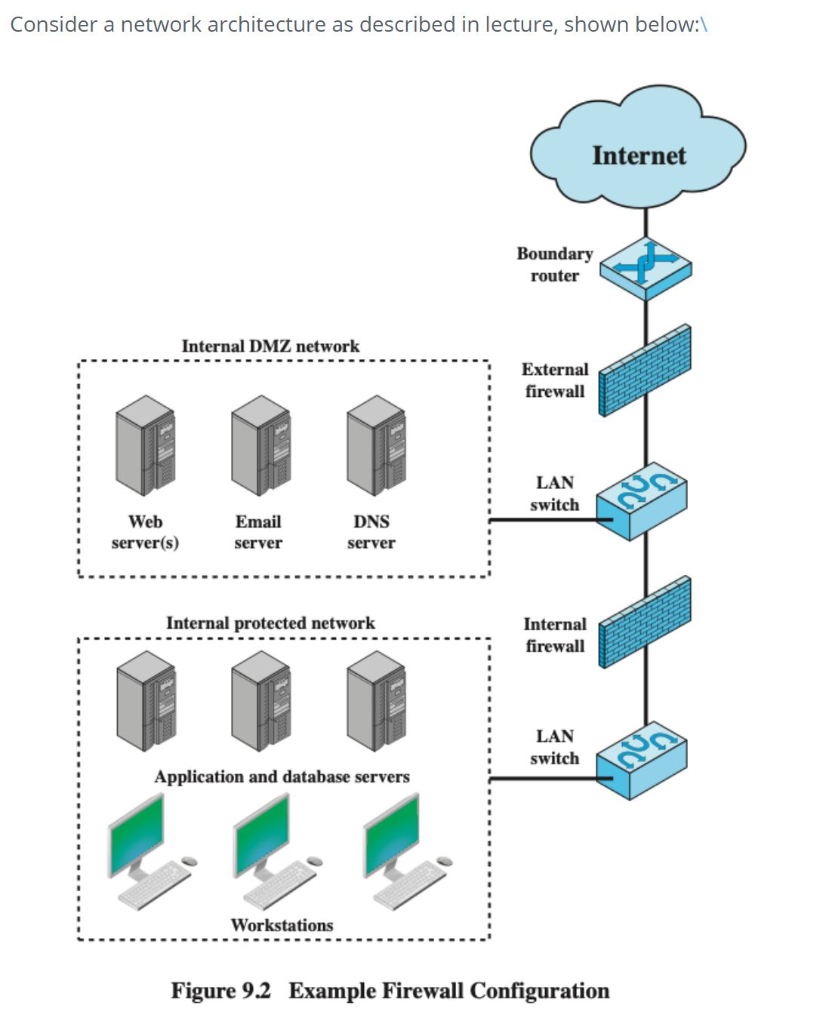
The easiest way to setup a DMZ is to use a firewall that has three or more network interfaces in the three legged DMZ model. In this configuration each of the interfaces will be assigned one of the following roles: internal network, DMZ network, and the external network (Internet). Typically a four-port Ethernet card in In a DMZ (DeMilitarized Zone) network! 2.2.2 The "Three-Homed Firewall" DMZ Architecture. At its simplest, a DMZ is any network reachable by the public but isolated from one's internal network. Ideally, however, a DMZ is also protected by the firewall. Figure 2-2 shows my preferred Firewall/DMZ architecture. Figure 2-2. The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone (DMZ) ... A DMZ interface is added according to the network diagram shown in Figure 10-1, with the configuration shown in Example 10-2. Figure 10-1 Adding a DMZ Interface to a Firewall
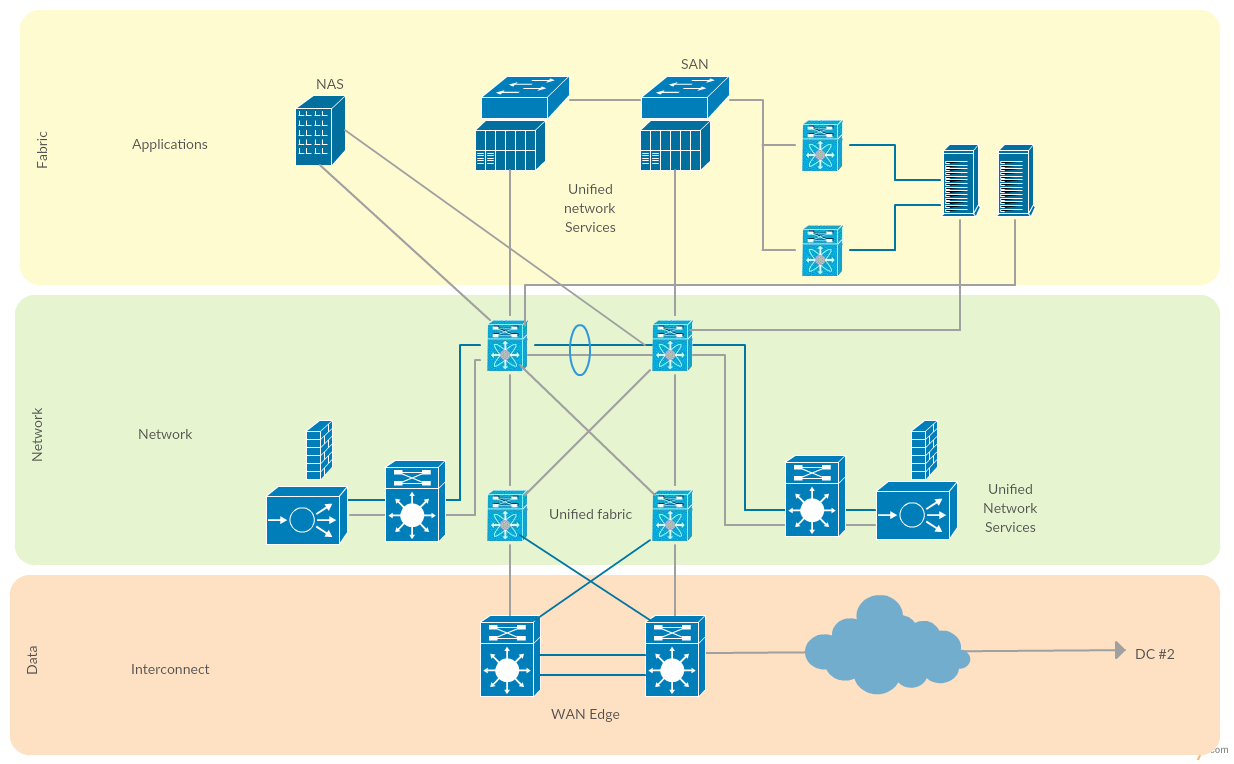
A local area network (LAN) is a devices network that connect with each other in the scope of a home, school, laboratory, or office. Usually, a LAN comprise computers and peripheral devices linked to a local domain server. All network appliances can use a shared printers or disk storage. A local area network serve for many hundreds of users. Typically, LAN includes many wires and cables that ...
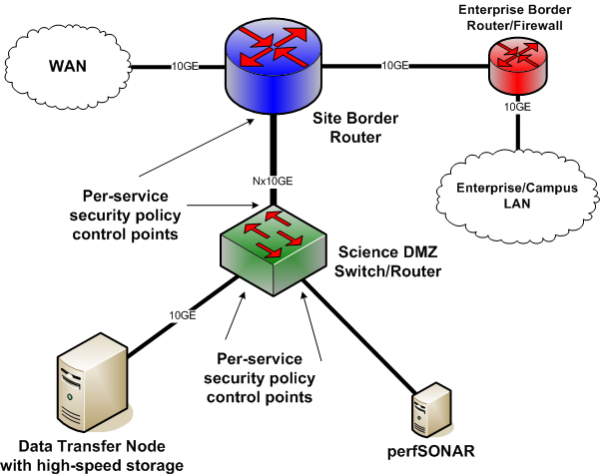
The DMZ will be placed Inside of this firewall. The tier of operations is as follows: the external network device makes the connection from the ISP, the internal network is connected by the second device, and connections within the DMZ is handled by the third network device.
Click on the Network Diagram header in the top left corner of the screen. A pop-up screen opens, type the name of your diagram in the text box and click OK. The name of your network diagram appears in the top left corner of the screen. 3. Remove existing elements that you don't need on your diagram.
Network diagrams can be used to represent virtually any network, which means that there's a lot of variety. Network diagrams vary in two important ways: by the type of network they represent and by network topology, or the arrangement of components. Below are a few examples, and you can always visit our network diagram example library for more.
The example of the network diagram below shows network architecture with configuration usually called "two firewall demilitarized zone". Demilitarized zone (DMZ) is a host or network segment located in a "neutral zone" between the Internet and an organization's intranet (private network).
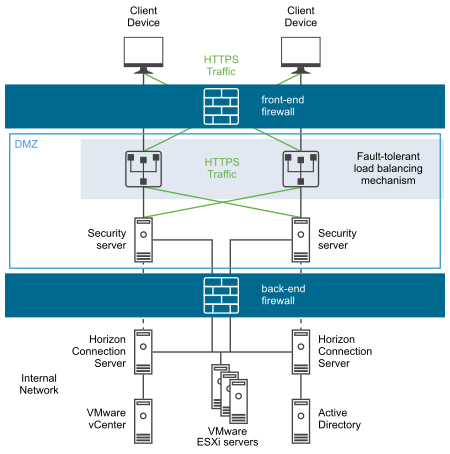
The two are functionally equivalent - the DMZ is effectively in a sandwich, as it has to have connections from the outside world firewalled, but also have firewalls restricting access from it to the internal network. While the latter diagram is often what happens (for cost reasons - you need less firewalls) the first one is considered safer as ...
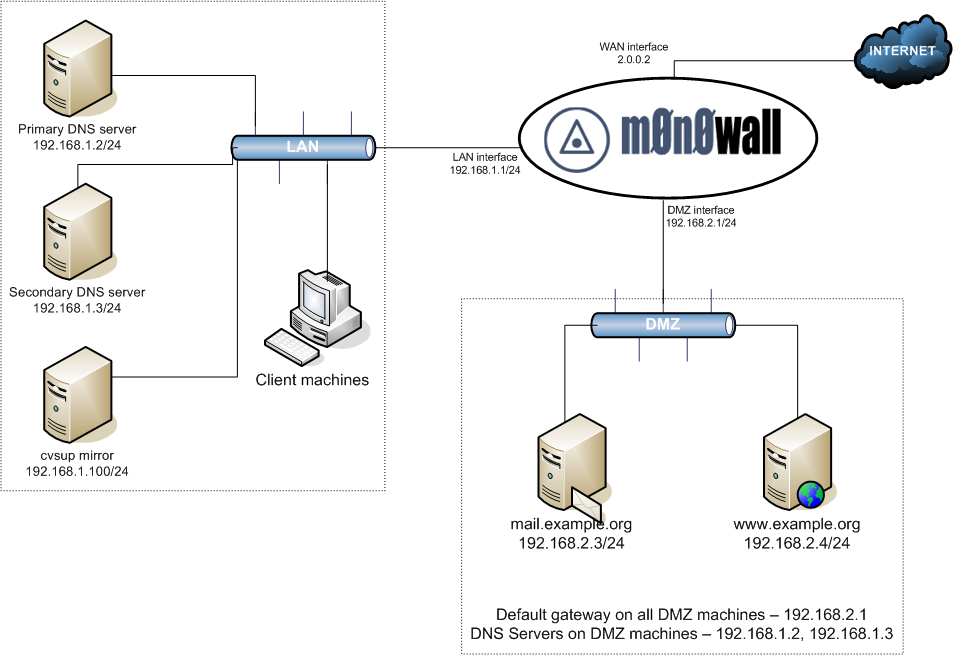
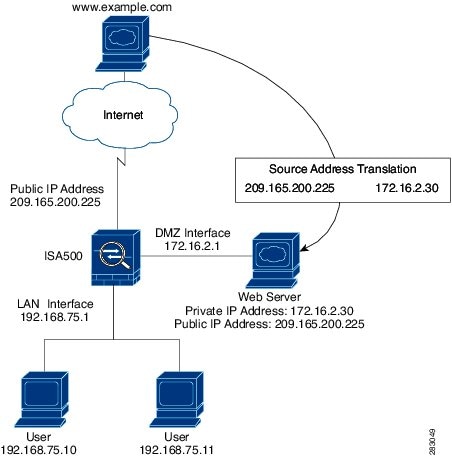
The 1:1 NAT DMZ setup is most appropriate where you have multiple public IP's and wish to assign a single public IP to each DMZ host. 13.1.1. Network Diagram. Figure 13.1. Example Network Diagram. This depicts the network layout we will have after configuring our DMZ interface. 13.1.2. Adding the Optional Interface.
Here's a diagram of the final DMZ network setup: This configuration is also known as the three-legged model. To take security up a notch, you can also use two firewalls (the back-to-back model). In this setup, one of the firewalls will allow traffic destined to the DMZ only, while the other only allows traffic to the DMZ from the internal ...
Common items that are placed in a DMZ are public-facing servers. For example, if an organization maintains its website on a server, that web server could be placed in a computer "Demilitarized Zone." In this way, if a malicious attack ever compromises the machine, the remainder of the company's network remains safe from danger.
In computer security, a DMZ or demilitarized zone (sometimes referred to as a perimeter network or screened subnet) is a physical or logical subnetwork that contains and exposes an organization's external-facing services to an untrusted, usually larger, network such as the Internet.The purpose of a DMZ is to add an additional layer of security to an organization's local area network (LAN): an ...
In computer networks, a DMZ, or demilitarized zone, is a physical or logical subnet that separates a local area network (LAN) from other untrusted networks ...
I'll assume that you have read some of the other posts on Network Diagrams and know how to put this diagram together. Start by drawing the box that you want to represent the area: Duplicate that box (Control-D), and rotate (Control-R) and then make it a bit smaller with your mouse. Now select all the three objects, then Shape, Operations, Union.
The example uses Visio-like Network Diagram shapes. Use MyDraw to create your own network diagram designs. Download Template: We use cookies to allow us to automate the access and the data entry functions of our website and to correlate online ordering information for purchases you may make while at the website (if any), tailor our website to ...
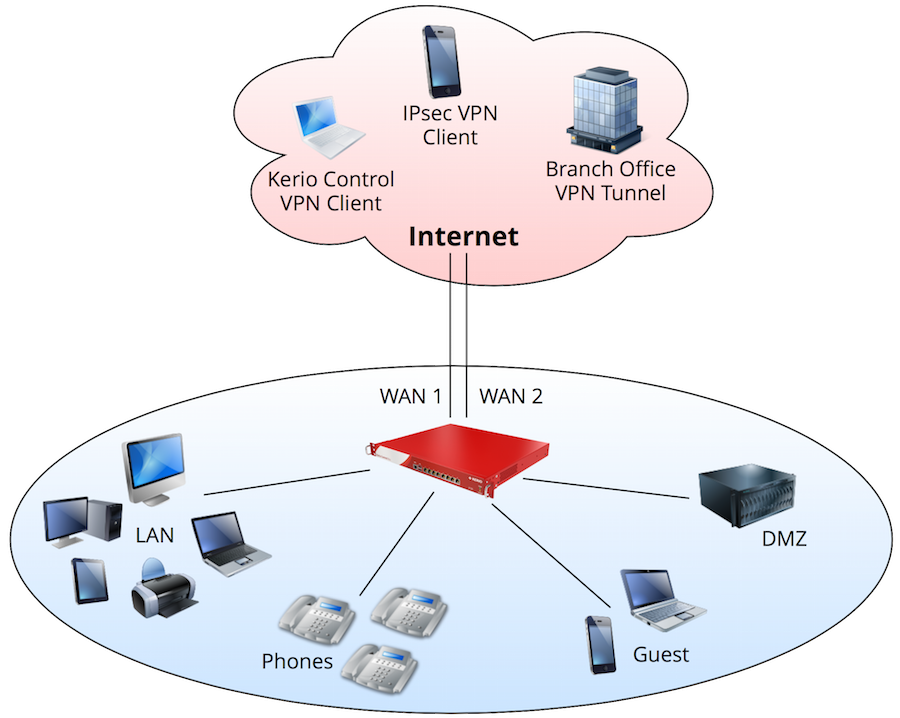
Configuring DMZ. Use the Networking > DMZ page to configure a Demarcation Zone or Demilitarized Zone (DMZ). A DMZ is a sub-network that is behind the firewall but that is open to the public. By placing your public services on a DMZ, you can add an additional layer of security to the LAN.
You will need to have a 3rd Ethernet port available in order to create another physical network. This physical network example uses 3 ports: 1 for the WAN, 1 for the LAN, and 1 for the DMZ network. Assign DMZ Interface. To assign a new interface for the DMZ network, go to the "Interfaces > Assignments" page.
Download scientific diagram | A medium size network with a DMZ. from publication: Improving ... Table 1 An example of rules on the Listed-Rule firewall.
The diagram highlights the simple traffic paths: outside can access the DMZ server but not the internal hosts, and if hosts need to access the DMZ they can. Moreover, the default interface level policy will not allow the untrusted network to source traffic towards the trusted network.
Sap Documentation Extended Online Search Sap Library Glossary Support Copyright Disclaimer Expand All Collapse All Previous Topic Next Topic Administration Manual Administration Manual J2ee Engine As Java Security An Overview Of The Security
Need Advise How To Create Dmz With Utm In My Home Network General Discussion Utm Firewall Sophos Community
















0 Response to "40 dmz network diagram example"
Post a Comment