40 network security architecture diagram
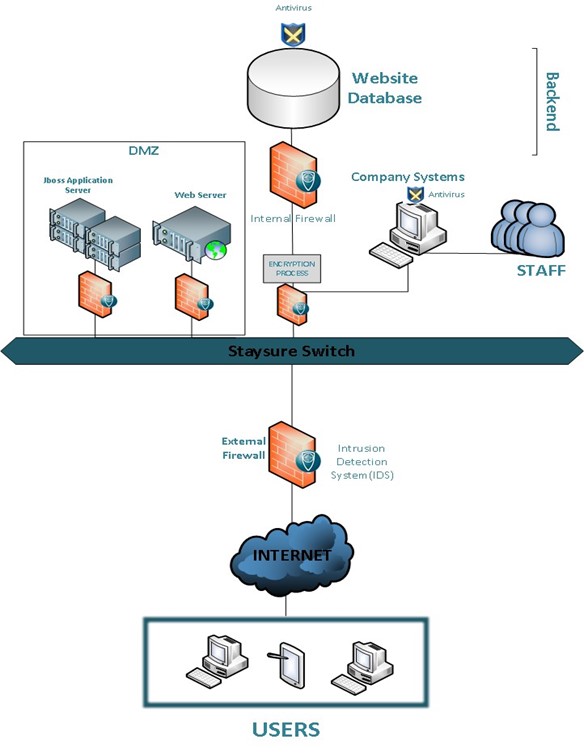
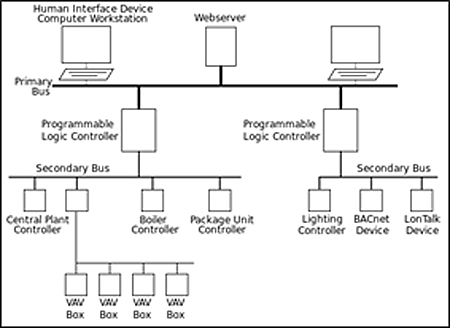
Network Security Architecture Diagram. Network security is the set of actions adopted for prevention and monitoring the unauthorized access, ensuring information security and defense from the attacks, protection from misuses and modification of a network and its resources. Network Security Architecture Diagram visually reflects the network's structure and construction, and all actions undertaken for ensuring the network security which can be executed with help of software resources and ... Figure 1 presents a notional enterprise architecture with two high-value systems residing in a high security zone (HSZ). The HSZ security devices provide boundary protection for the high-value systems in addition to protections provided at the enterprise level, such as the security devices between the enterprise network and the internet and DMZ.
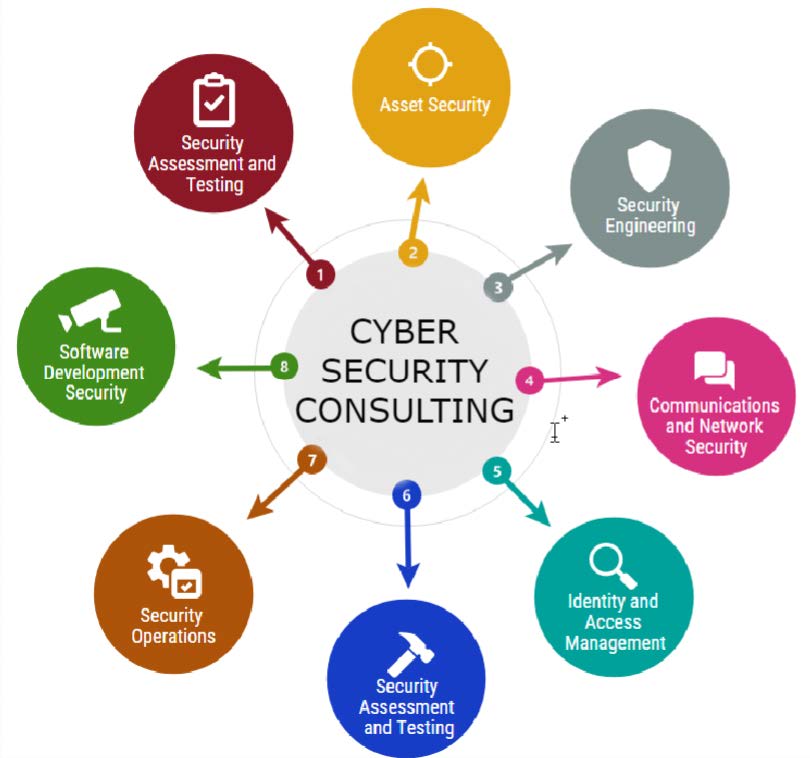
Network Security Components and Reference Architectures Subject This document contains components critical for network security and provides a number of use cases and architectures for Intent Based Segmentation which aligns business goals with what is achievable on the network.
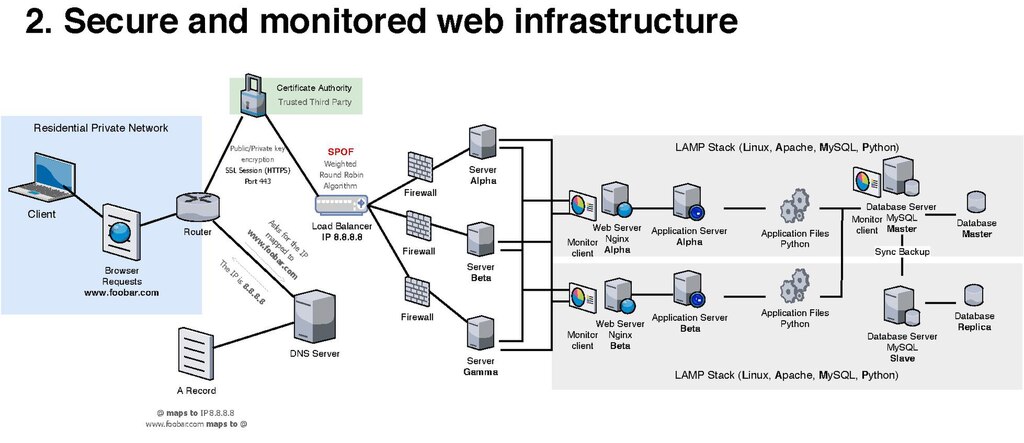
Network security architecture diagram
Network diagrams refer to the documentation that identifies the flow of data within an organization. Project managers often refer to network diagrams more broadly, but in the case of cybersecurity, it pertains to data flow across telecommunication hardware. These network infrastructure diagrams are essential to any cybersecurity program. Without this information, CISOs and security advisors cannot identify system vulnerabilities. Network diagrams exist in two parts or topologies: 1. Physical Topologies 2. Logical Topologies May 4, 2016 - The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons. It will help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics, Network Plans for secure wireless network, Computer Security Diagrams to share knowledge about effective ways of networks ... This is defined as the part of enterprise architecture that is particularly design for addressing the information system and fulfill the security requirements of the organization. The system architecture system has a role that it meets the security requirements and also helps to protect the company operating environment. It is beneficial for the company as it includes other activities like risk management activities that require continuous improvement, and security architecture helps to meet the organization requirements. It defines proper polices, rules and regulations that need to reinforce in the organization and provide proper information about them. The architecture is also used for allocating the controls for technical security so that the information system of the organization can be maintained properly. As the same can be followed in a whole organization, it helps to define common regulations and standards for every employee so that everyone can follow the rules and maintain...
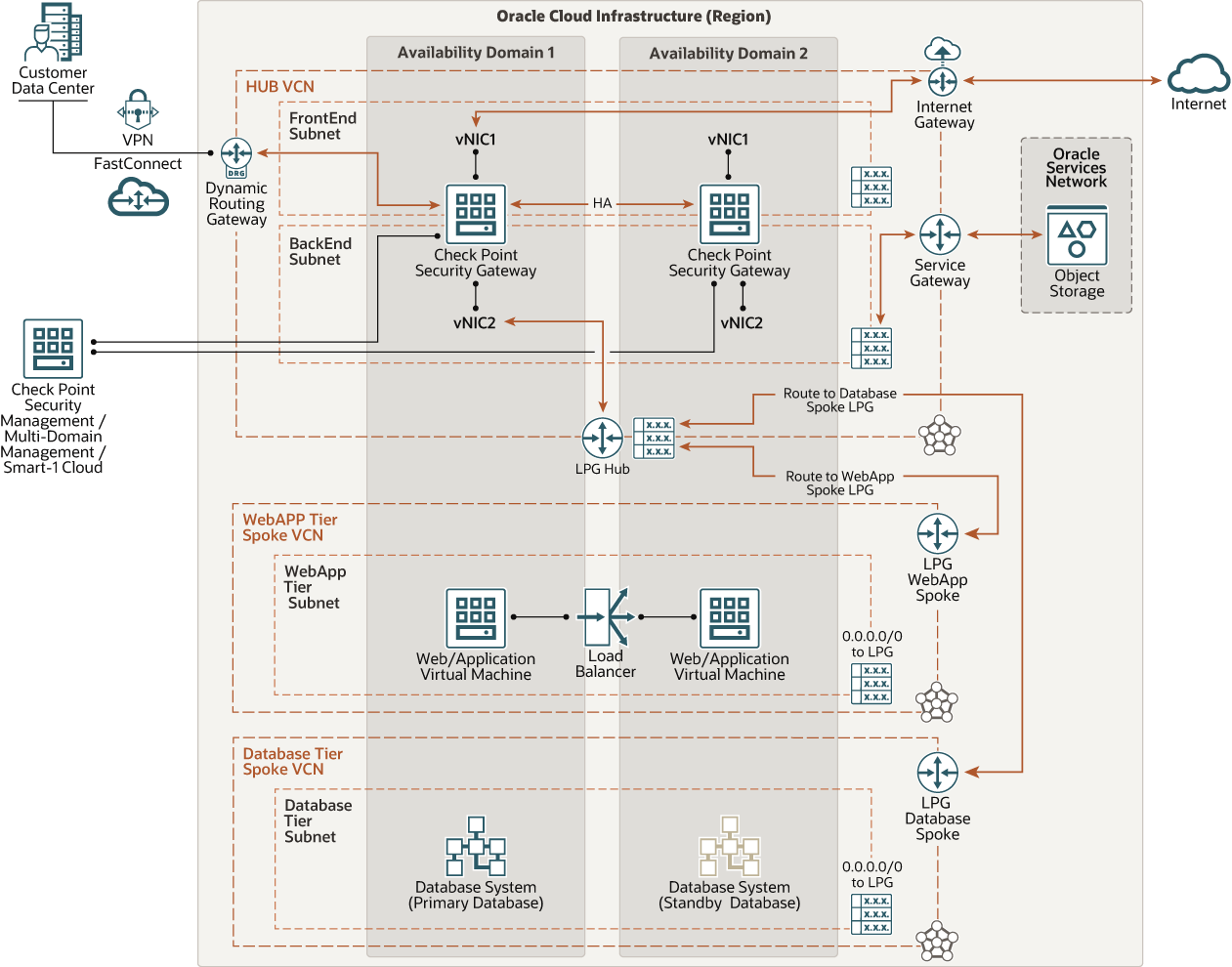
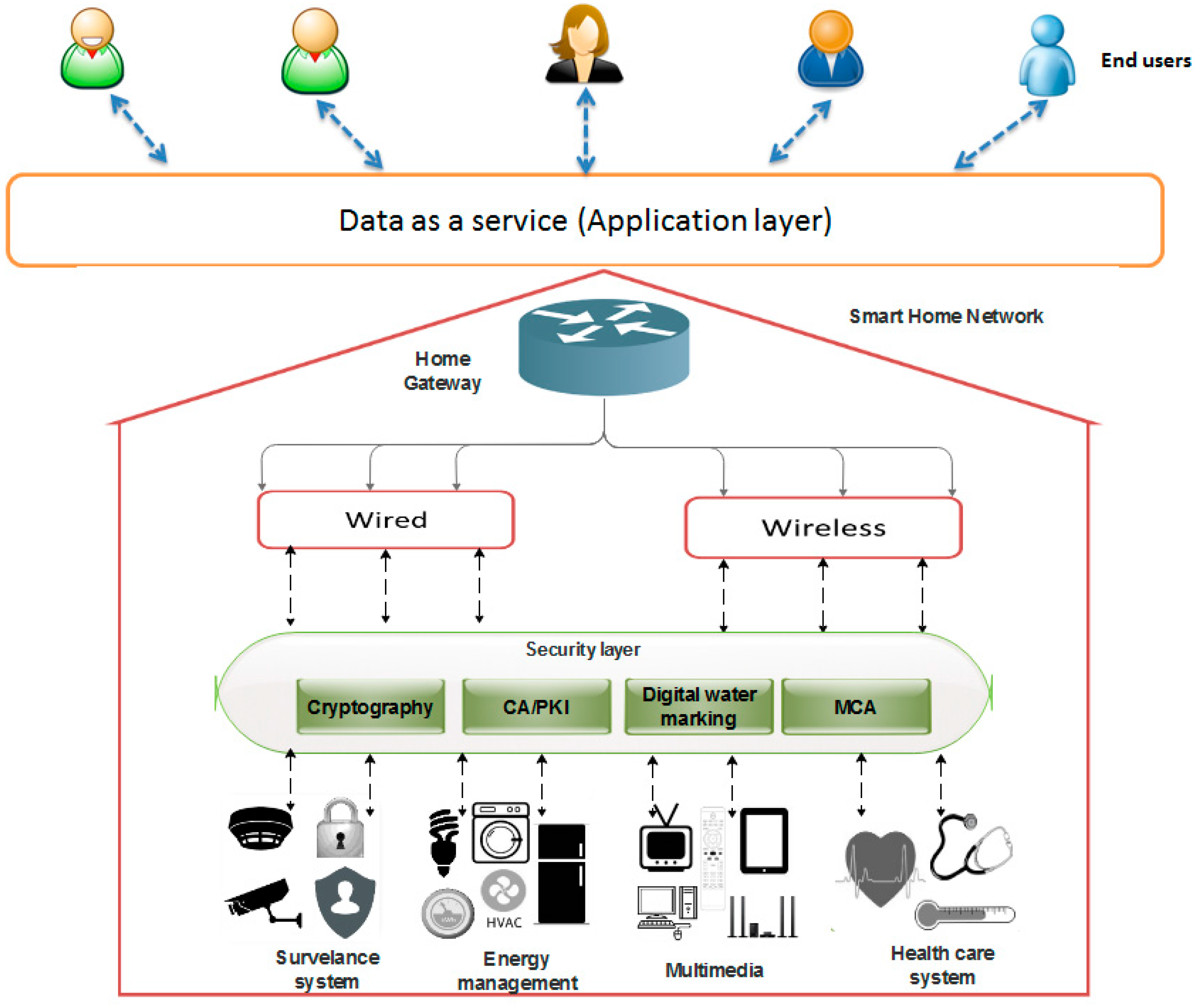
Network security architecture diagram. Segment your network footprint and create secure communication paths between segments. Align the network segmentation with overall enterprise segmentation strategy. Design security controls that identify and allow or deny traffic, access requests, and application communication between segments. Protect all public endpoints with Azure Front Door ... 4 802.11 or Wi-Fi IEEE standard for wireless communication −Operates at the physical/data link layer −Operates at the 2.4 or 5 GHz radio bands Wireless Access Point is the radio base station −The access point acts as a gateway to a wired network e.g., ethernet −Can advertise Service Set Identifier (SSID) or not Doesn't really matter, watcher will learn active Use a microservices architecture to develop cloud-native mobile and web applications. Create secure solutions that connect and manage edge devices at scale and provide analytics in the devices at the source of the data. Move computation towards the edge of the network for improved transfer rates and response times. 28.10.2021 · Network security architecture diagram. Applications In our previous IDE. Network Security Architecture Diagram. If you were to ask network architects and engineers about their favorite part of the job I doubt any of them will respond with creating and maintaining network diagrams Its not the most glamorous taskyet requirements 112 and 113 of the …
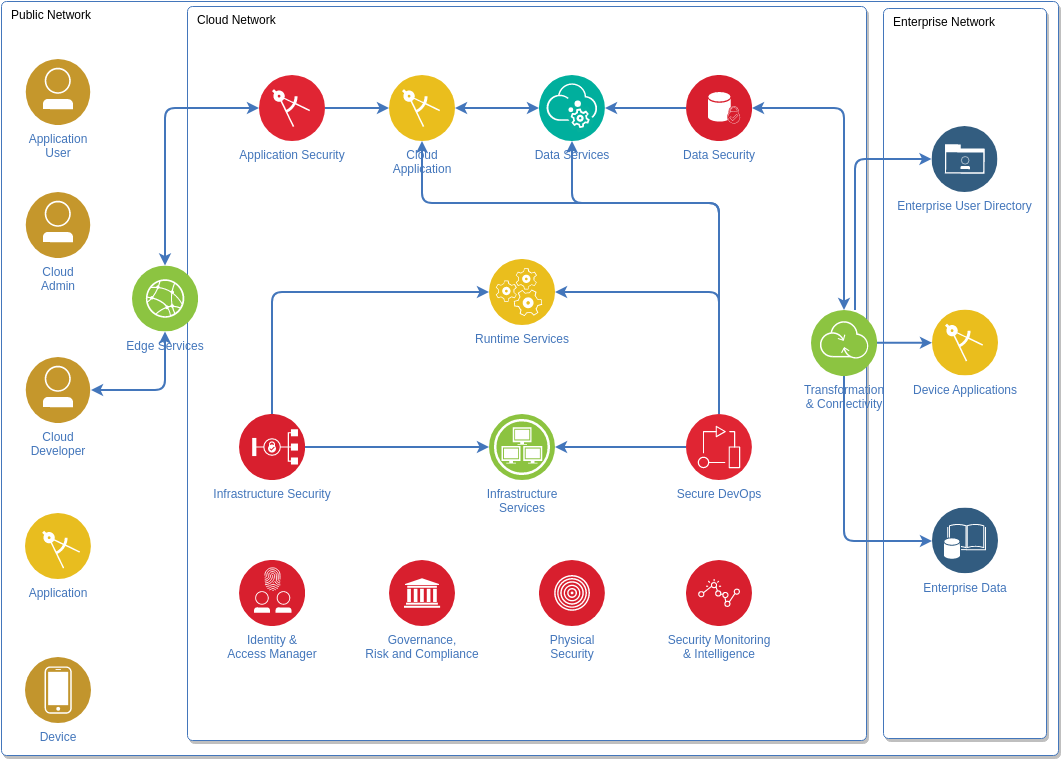
Network automation architecture. Move computation towards the edge of the network for improved transfer rates and response times. The major components in a network automation architecture are the hardware resources, virtualization layer, management and orchestration, OSS/BSS, and applications. This diagram shows how to deploy Siemens NX on Amazon AppStream 2.0 by leveraging Amazon EBS volumes for shared folders, using Amazon FSx for a highly-performant file system. Includes how to extend the Amazon FSx solution to multi-Region deployments. PDF. The Microsoft Cybersecurity Reference Architecture describes Microsoft’s cybersecurity capabilities and how they integrate with existing security architectures and capabilities. We recently updated this diagram and wanted to share a little bit about the changes and the document itself to help you better utilize it. Network Intrusion Detection Systems (NIDS) function similar to an activated security alarm system that watches for known behaviors (signatures), which indicate suspicious acti vity and even system break -ins. NIDS is a critical component for any secure network architecture; providing a key extra layer of defense to a properly designed network.
What is network architecture diagram? — The network diagram depicts the network architecture in visual form. In a network diagram, there are a variety ... The DOE IT Security Architecture approaches IT Security as a distinct set of business activities ... routinely flows in and out of a network through . IT Security Architecture February 2007 6 numerous access points. This separation of information from systems requires that the N etwork architecture is the physical and logical design of a computer network. This framework is often represented with a diagram to provide the precise description of an established network, and the system is designed by the network architect with the help of network engineers. The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons and connectors to help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics to share knowledge about effective ways of networks protection with help of software and network security devices of different cyber security degrees, Network Plans for secure wireless network, Computer Security Diagrams to ...
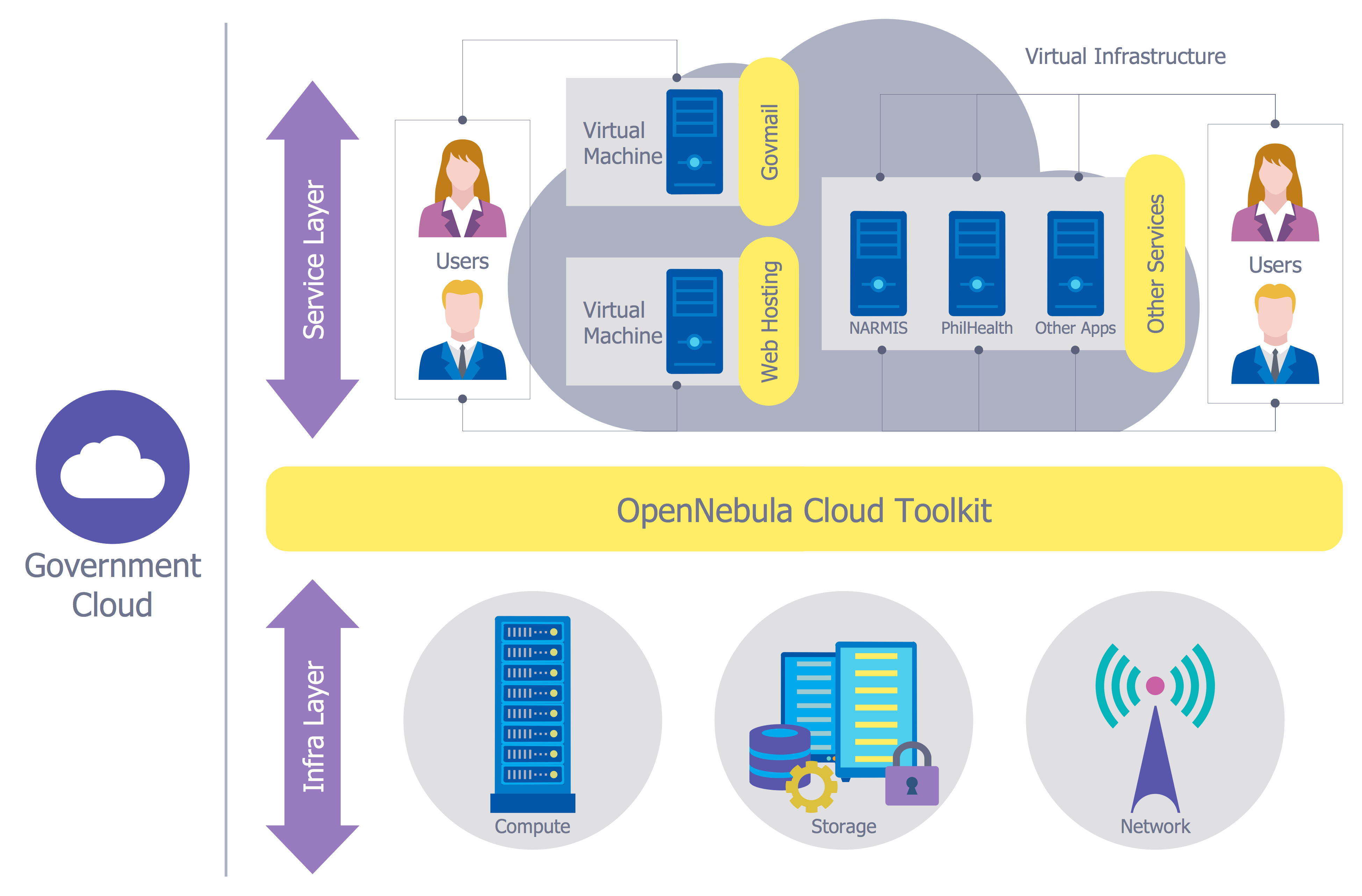
1 1 . NIST Special Publication 500-299 . 2 . 3 . 4 . 5 . NIST Cloud Computing 6 . Security Reference Architecture 7 . 8 . 9 . 10 . 11 . 12 . NIST Cloud Computing ...
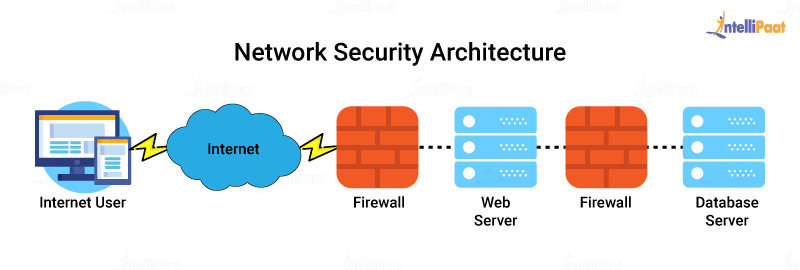
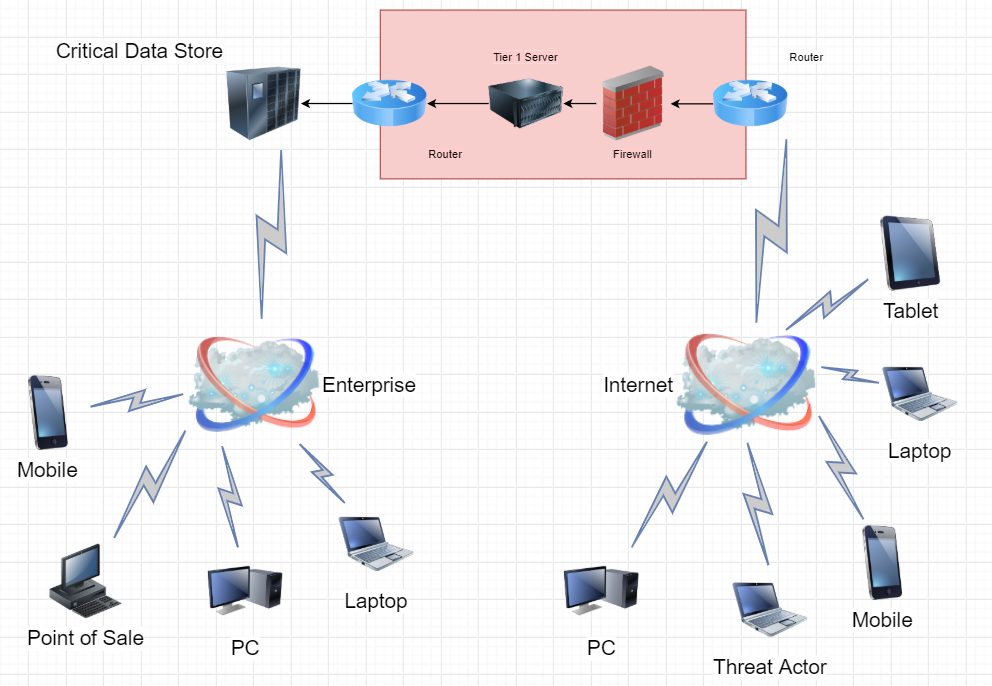
Basic Internet Network Architecture Practices. The typical architectural diagram shown below offers only two slim layers of protection, yet it is widely accepted that more layers equal a more secure environment. In the diagram below, an attacker must compromise only one server to gain access to the Web applications provided on the same system.
As an example of how one might create a Logical Security Architecture diagram, I'll take a random network diagram from the internet as a reference point for a fictional company. Note: This is not part of the SABSA process, but to merely utilize as a reference point of comparison of what others in an IT field would be used to seeing vs one based ...
Cisco’s Network Security Architecture Borderless Data Center 3 Borderless Internet 2 Borderless End Zones 1 Policy Corporate Border Branch Office Applications and Data Corporate Office Policy 4 (Access Control, Acceptable Use, Malware, Data Security) Home Office Attackers Coffee Customers Shop Airport Mobile User Partners
We have seen these diagrams used for several purposes including. Starting template for a security architecture - The most common use case we see is that organizations use the document to help define a target state for cybersecurity capabilities. Organizations find this architecture useful because it covers capabilities across the modern ...
A network architecture diagram, also known as a network infrastructure diagram, helps admins visualize their complete network infrastructure and architecture. It provides a comprehensive picture of resources and network layers, potentially including hardware, layout and topology, wireless connections, software, protocols, and more.
Many organizations struggle to implement the secured Network Architecture that can optimize the Network Security. Organizations usually spend a lot of time, effort, and money deploying the latest ...
NI -1 Network Connectivity Diagram C3/R5 NI -2 Network Inventory C3/R5 NI -3 Capital Equipment Inventory C3/R5 NI -4 Building Blueprints * C3/R5 NI -5 Network Center Diagram C3/R5 NI -6 Cable Plant Diagram C3/R5 NI -7 Rack Elevation Diagram C3/R5 Security (SP)
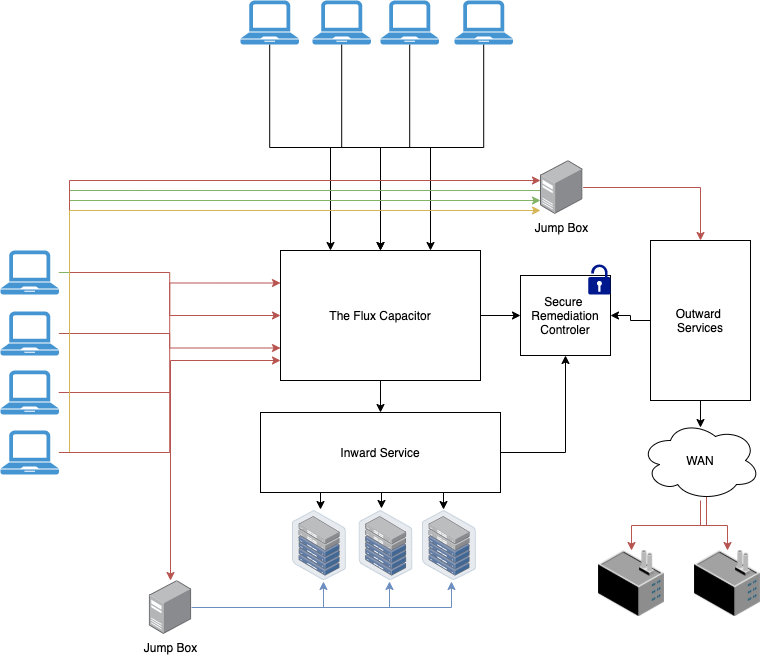
Network IPS scenario Summary Identification of security domains basis of perimeter security control Firewall is the main enforcer Intrusion detection introduces deeper analysis and potential for more dynamic enforcement Intermediate enforcement can handle some Denial of Service attacks Network Security Architecture CS461/ECE422 Computer ...
Sep 15, 2020 · Vital Role of Network Architecture Diagram. When it comes to troubleshooting network configurations, a network architecture diagram removes the guesswork out of the equation. It saves resources such as money and time when it comes to restarting a network.
Download scientific diagram | OPENFLOW NETWORK SECURITY ARCHITECTURE from publication: A Security Architecture Proposal for Detection and Response to ...
If you were to ask network architects and engineers about their favorite part of the job, I doubt any of them will respond with "creating and maintaining network diagrams." It's not the most glamorous task—yet requirements 1.1.2 and 1.1.3 of the Payment Card Industry Data Security Standard (PCI DSS), along with general good security hygiene, render it a necessary one.
Most architecture diagrams focus and dive deep on the web, application, and data tiers. For readability, they often omit the security controls. This diagram flips that emphasis to show security wherever possible, and keeps the application and data tiers as simple as necessary to show security features meaningfully.
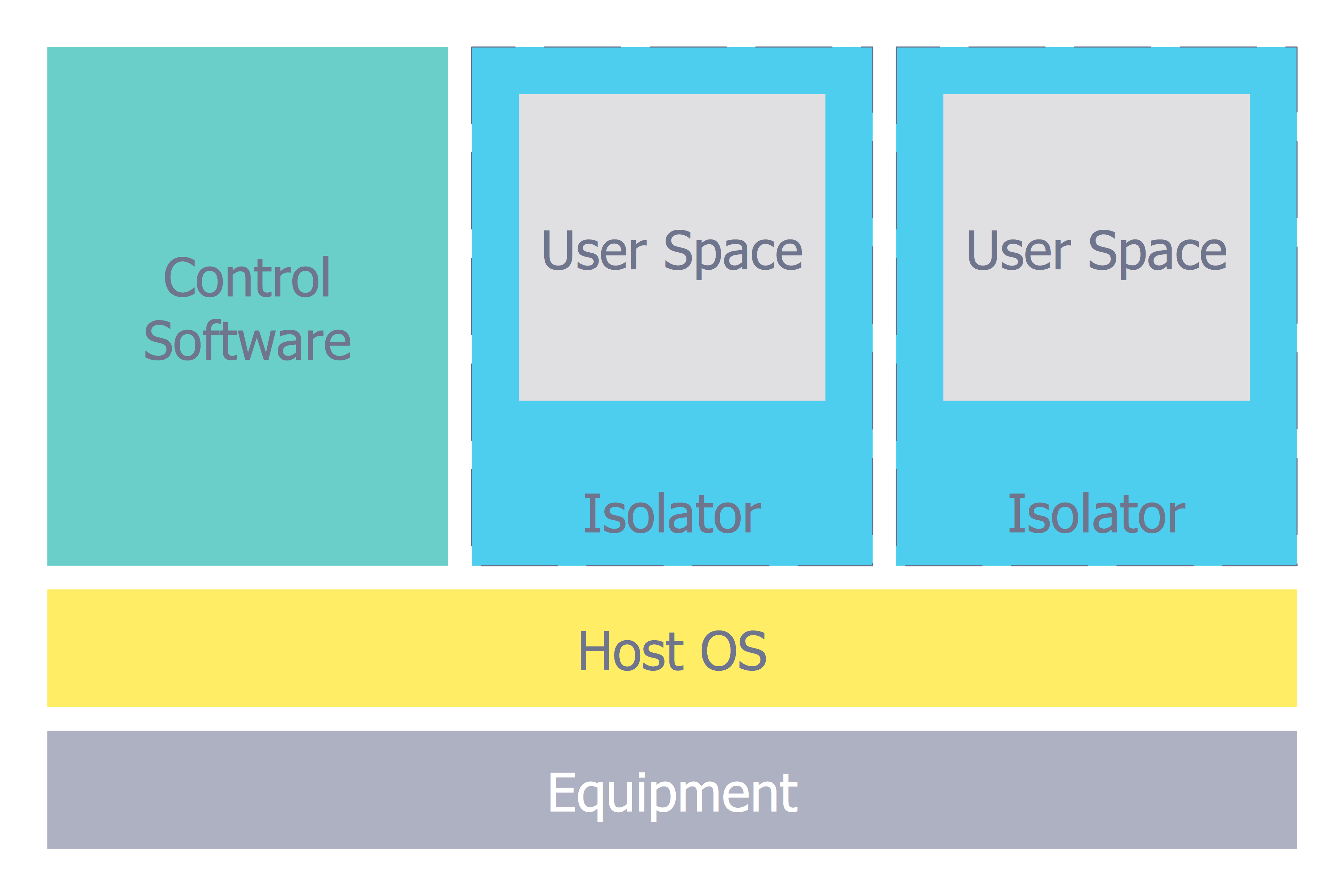
Network Security) is an example of network layering. Unlike the OSI model, the layers of security architecture do not have standard names that are universal across all architectures. A generic list of security architecture layers is as follows: 1. Hardware 2. Kernel and device drivers 3. Operating System 4. Applications In our previous IDE !
This is defined as the part of enterprise architecture that is particularly design for addressing the information system and fulfill the security requirements of the organization. The system architecture system has a role that it meets the security requirements and also helps to protect the company operating environment. It is beneficial for the company as it includes other activities like risk management activities that require continuous improvement, and security architecture helps to meet the organization requirements. It defines proper polices, rules and regulations that need to reinforce in the organization and provide proper information about them. The architecture is also used for allocating the controls for technical security so that the information system of the organization can be maintained properly. As the same can be followed in a whole organization, it helps to define common regulations and standards for every employee so that everyone can follow the rules and maintain...
May 4, 2016 - The Network Security Diagrams solution presents a large collection of predesigned cybersecurity vector stencils, cliparts, shapes, icons. It will help you succeed in designing professional and accurate Network Security Diagrams, Network Security Infographics, Network Plans for secure wireless network, Computer Security Diagrams to share knowledge about effective ways of networks ...
Network diagrams refer to the documentation that identifies the flow of data within an organization. Project managers often refer to network diagrams more broadly, but in the case of cybersecurity, it pertains to data flow across telecommunication hardware. These network infrastructure diagrams are essential to any cybersecurity program. Without this information, CISOs and security advisors cannot identify system vulnerabilities. Network diagrams exist in two parts or topologies: 1. Physical Topologies 2. Logical Topologies



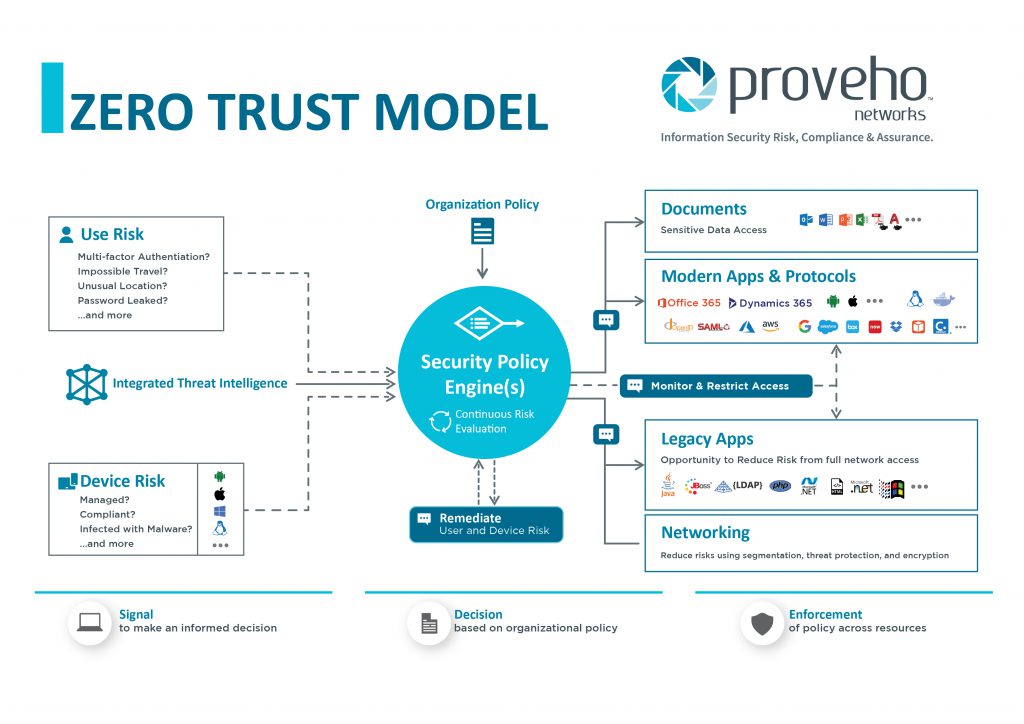

![PDF] Construction of Network Security Architecture Based on ...](https://d3i71xaburhd42.cloudfront.net/0940af937eac9f9f90fbabe5193f672acc95c067/5-Figure4-1.png)
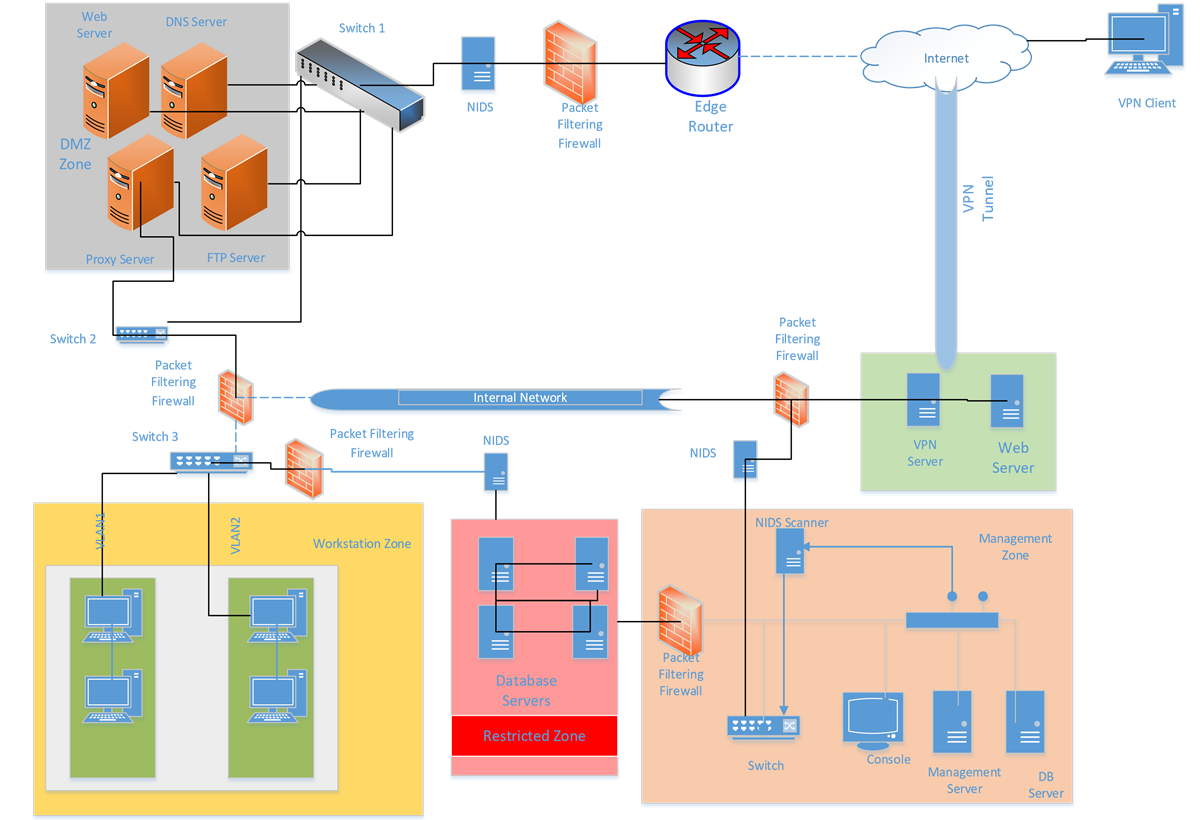











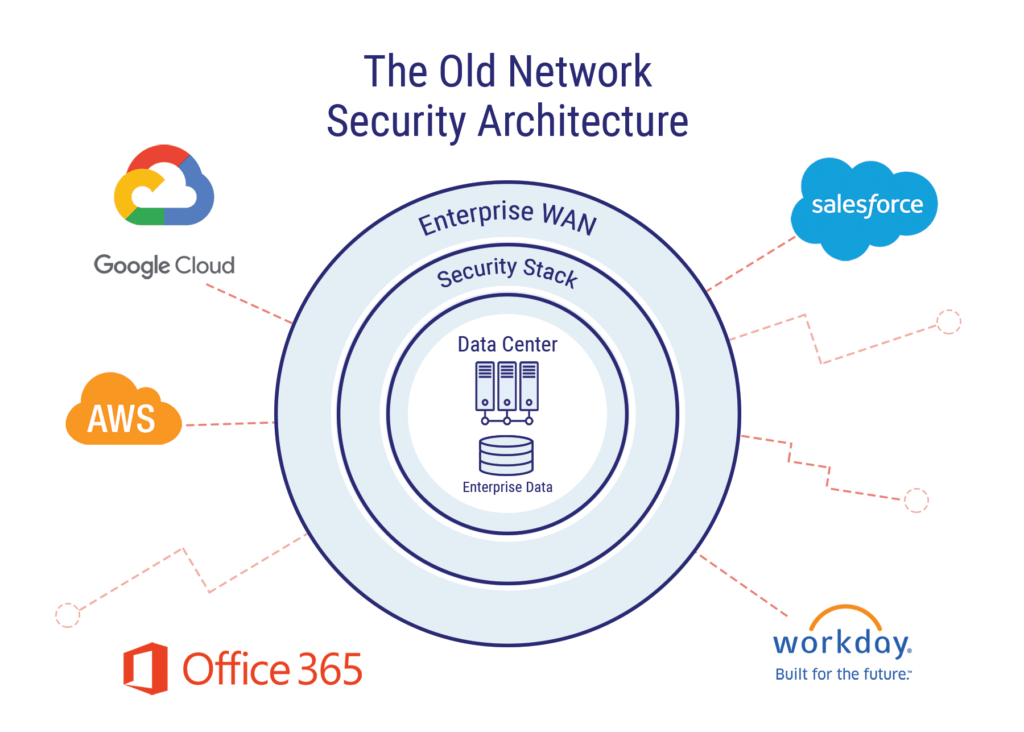


0 Response to "40 network security architecture diagram"
Post a Comment